
Welcome to our comprehensive guide on performing Cross-Site Scripting (XSS) testing with a professional Website Security Tester. In today’s digital environment, protecting your website against vulnerabilities such as XSS is critical to preserving trust, integrity, and security.
XSS attacks can have serious implications, including the compromise of user data, reputational damage, and even legal ramifications. You may successfully reinforce your defenses and reduce the danger of XSS vulnerabilities by employing the expertise of a Website Security Tester.
Table of Contents
ToggleWhat exactly is Cross-Site Scripting (XSS)

Cross-site scripting (XSS) is a vulnerability in the web’s security that enables an attacker to compromise user interactions with a susceptible application. It enables an attacker to bypass the same origin policy, which is intended to separate various websites. Cross-site scripting vulnerabilities typically enable an attacker to impersonate a target user, conduct any activities that the user is capable of, and gain access to any of the user’s data. If the target user has privileged access to the program, the attacker may be able to take complete control over all of its functionality and data.
What is the cross-site scripting in XSS?
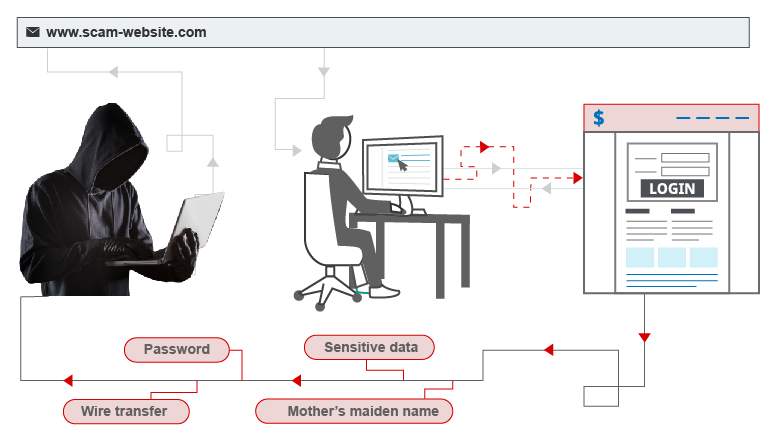
Cross-site scripting operates by modifying a vulnerable website so that users receive malicious JavaScript. When the malicious code executes within a victim’s browser, the attacker has complete control over their interaction with the program.
Most XSS vulnerabilities may be confirmed by inserting a payload that allows your browser to run arbitrary JavaScript. It’s long been usual practice to utilize the alert() method for this purpose because it’s brief, innocuous, and difficult to miss when used correctly. In fact, you can solve the bulk of our XSS experiments simply using alert() in a simulated victim’s browser.
What are the different forms of XSS attacks?
There are three major forms of XSS attacks. They are:
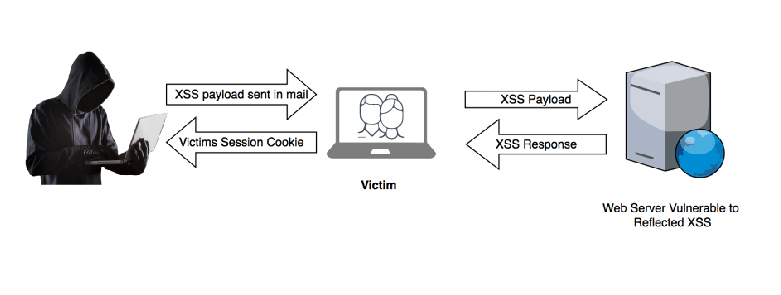
- Reflected XSS, in which the malicious script originates from the current HTTP request.
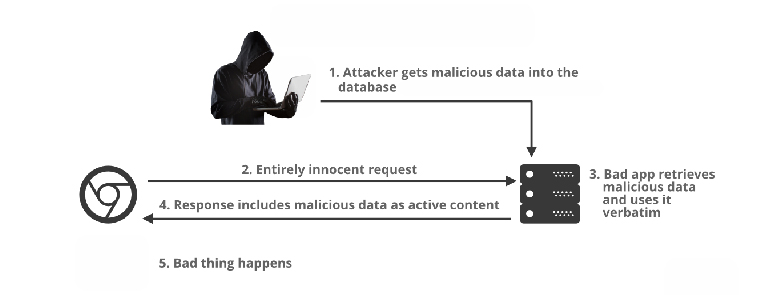
- Stored XSS, with the malicious script originating from the website’s database.
- DOM-based XSS occurs when the vulnerability exists in the client’s code rather than on the server side.
Which objective can XSS serve?
An attacker that exploits a cross-site scripting vulnerability can often do the following:
- Impersonate or pose as the affected user.
- Carry out any activity that the user is capable of performing.
- Read any data that the user may access.
- Capture the user’s login information.
- Perform virtual defacement on the website.
- Integrate Trojan functionality into the website.
The impact of XSS vulnerabilities
The actual effect of an XSS attack is determined by the application’s nature, functionality, and data, as well as the compromised user’s status. For example:
- The impact of a brochureware application, in which all users are anonymous and all information is public, is frequently modest.
- The impact on an application that stores sensitive data, such as financial transactions, emails, or healthcare information, is frequently severe.
- If the affected user has elevated rights inside the program, the impact will be severe, allowing the attacker to gain complete control of the vulnerable application and compromise all users’ data.
How to Identify and Test for XSS vulnerabilities
Manually testing for reflected and stored XSS typically entails entering some simple unique input (such as a short alphanumeric string) into each entry point in the application, identifying every location where the submitted input is returned in HTTP responses, and testing each location individually to see if suitably crafted input can be used to execute arbitrary JavaScript. This allows you to identify the context in which the XSS happens and choose an appropriate payload to exploit it.
Manually testing for DOM-based XSS coming from URL parameters follows a similar procedure: provide some basic unique input into the parameter, use the browser’s developer tools to search the DOM for this input, and test each place to see whether it is exploitable. However, some kinds of DOM XSS are more difficult to detect.
To detect DOM-based vulnerabilities in non-URL-based input (such as document.cookie) or non-HTML-based sinks (such as setTimeout), there is no replacement for studying JavaScript code, which can take a long time. Burp Suite’s online vulnerability scanner uses static and dynamic JavaScript analysis to consistently find DOM-based vulnerabilities.
How to avoid XSS attacks
Preventing cross-site scripting is simple in certain circumstances, but it can be considerably more difficult depending on the sophistication of the program and how it handles user-controllable data.
In general, properly avoiding XSS vulnerabilities may entail a mix of the following measures:
- Filter input upon arrival. When you get user input, filter it as precisely as feasible based on what is anticipated or legitimate.
- Encode data on output. When user-controllable data is produced in HTTP replies, encrypt the output to avoid it from being misinterpreted as active content. Depending on the output context, this may need combining HTML, URL, JavaScript, and CSS coding.
- Content Security Policy. As a last line of protection, you may employ Content Security Policy (CSP) to mitigate the severity of any remaining XSS vulnerabilities.
Conclusion
Finally, hiring a professional Website Security Tester is not only a preventive strategy, but also a must-have for protecting your online assets. You may safeguard your website and users from harmful attacks by doing extensive XSS testing and putting in place strong security protocols. Don’t wait until it’s too late; take proactive efforts today to strengthen your defenses and provide a safe digital environment for your company and customers. Contact us now to learn more about how our Site Security Tester service may help you keep ahead of threats and retain your peace of mind.
XSS vulnerabilities have become general, and XSS is likely the most common online security flaw.
It is difficult to obtain solid data on real-world XSS attacks, however they are likely less commonly exploited than other vulnerabilities.
XSS is a client-side vulnerability that affects other application users, whereas SQL injection is a server-side vulnerability that attacks the program’s database.
Cross-site scripting, or XSS, is perhaps the most frequent online security problem. It allows an attacker to inject client-side scripts (such as Javascript, VBScript, or Flash) into web pages viewed by other users that can be fixed by a Website Security Tester.
Manually testing for reflected and stored XSS typically involves submitting some simple unique input (such as a short alphanumeric string) into each entry point in the application, identifying every location where the submitted input is returned in HTTP responses, and testing each location individually.




